Social Media Security: Avoid This Social Engineering Ploy
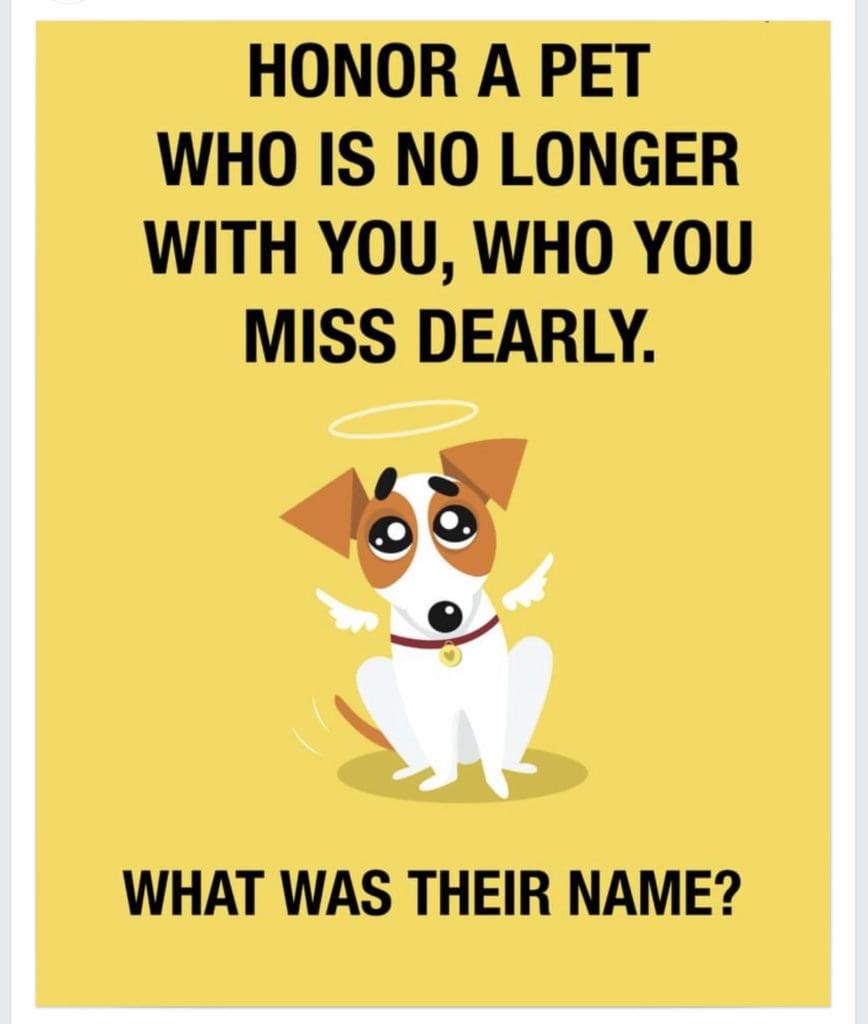
Social media security is about far more than protecting your password. It’s about being aware and careful about what information you share online. Consider this innocent post found recently on Facebook: Isn’t this a nice sentiment? If you’re a pet lover and have lost one, you’ll probably comment without thinking. Look at all these people who miss their pets, too! But that simple comment is a huge cyber security risk.
Social media challenges: not all fun and games
This post and others like it are a social engineering ploy to gather information about you. You read that correctly. It’s a gimmick to trick you and it doesn’t have to be specifically about a pet. It could be something about a former address, street names, high school mascot, favorite movie or even the name of a childhood best friend. All of these answers and more give criminals a lot of information — especially when cross referenced with all the other data you have shared on your social media profiles. And if you’re on any social media you have shared a lot of data.
But it doesn’t stop there. Have you been tempted to respond to a Facebook challenge? Maybe one that asks you to name your first seven jobs that you have held?
Or even this “Prove me wrong” puzzler:
BEWARE. They might be legit but they are most likely social engineering ploys.
How scammers make it work
These ploys can work in a few different ways (and sometimes more than one).
- You share info (like the pet’s name or first job) and it’s used to answer a challenge question to gain access to your account or discover more about your background.
- The post itself links off to a site that automatically downloads malware onto your computer. This can also happen with fake friend requests or even fake ads.
Don’t imagine that a criminal is scouring your social media and cross referencing that with every place you have an account and typing in a bunch of challenges until they get in. That’s possible, of course. But these days cyber criminals don’t have to do nearly that much work. What really happens, millions of times a day, is that data gets scraped from messages like this and dumped into a program that automatically challenges hundreds of accounts at a time until it gets in. These are called brute force attacks and criminals don’t even need to have hacking skills to run them. They just need to buy some software off the dark web.
Keep your social media safe with Aeko
As a managed service provider, part of what we do for clients is to provide ongoing cyber security training for their entire team. That’s because social engineering and phishing are the easiest way for criminals to gain access to your network. Training turns your biggest security risk (people) into your best cyber security assets — human firewalls who know how to spot and resist falling for posts like these. Let’s discuss the cyber security and IT support needs of your small or medium-sized business. Contact us or book a meeting for a no-pressure consultation with our experts.
Are you aware of the most common cyberattack methods?
Did you know there are over 3.4 billion phishing emails sent every day? Phishing and other cybercriminal behavior are a lot more common than you’d think.
Our free “Phishing, Smishing, Vishing, Pharming? A Cyberattacks Guide” will inform you about cyberattack methods and give you the latest in data security tips.

