
Don’t Be Confused by the Microsoft MFA Warning: The Bottomline on Multi-Factor Authentication
As cyber security experts, we agree with the Microsoft MFA warning. But don’t get confused into thinking all multi-factor authentication is dangerous. Here’s the full story.
What Is Multi-Factor Authentication (MFA)?
Multi-factor authentication (MFA) sounds a bit scary, but it’s actually pretty simple. You know that password you use to sign into your account? That is one-factor authentication. MFA requires more than just the password — multiple factors — to prove that you are, well… you.
Would you know what to do for a ransomware attack? Download our free Ransomware Response Checklist.
Multi-Factor Authentication (MFA) vs Two-Factor Authentication (2FA)
All MFA involves two-factor authentication (2FA), which combines something you know (like a password) with something you have in your possession.
This is what you are doing when you use your credit card at the gas pump and it prompts you to enter your zip code. The card (something you have) is one factor and the zip code (something you know) is another.
But as cybercrime has increased, so has the need for more sophisticated 2FA systems, which is why multi-factor authentication was born.
Types of Multi-Factor Authentication (MFA)
MFA By App
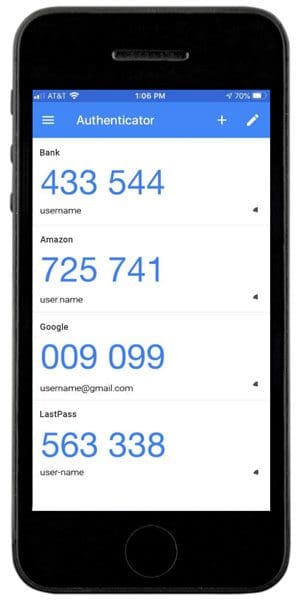
This is the most secure form of authentication that uses a phone and is NOT part of the warning recently issued by Microsoft. This method requires you to download an authenticator app which you then set up for each account as you activate MFA for that account.
When you want to log in to an account set up with MFA by app, you enter your username and password, then are prompted to enter the code from your app. You open the app, view or copy the code and then use it to access your account. Codes are different for each account and are refreshed every 30 seconds.
With MFA by app, even if your username and password are compromised, cyber criminals will not be able to access your account because they don’t have your phone with your authenticator app in their possession.
MFA by Text or Push Notifications
These are less secure methods of multi-factor authentication and ARE part of the warning recently issued by Microsoft. With MFA by text, when you sign in with your username and password, it triggers a code to be sent to your phone number by text (SMS). With push notifications, the code pops up as a notification on your phone instead of as a text message.
Here’s where the Microsoft warning tripped some people up: both MFA by text and by push notifications are better than having no MFA enabled at all.
That said, they are less secure than MFA by app because it is possible for cyber criminals to steal your phone number without ever getting a hold of your phone: a crime called SIM hijacking (or SIM swapping). SIM hijacking is on the rise, which is likely the reason for Microsoft’s warning. Learn more about SIM jacking.
If you need to choose one of these methods, MFA by text is better than MFA by push notification because the push messages are very inconsistent. Some require one click, some several and it can be easy to click by mistake, which may leave you open to clicking on a fake push notification.
If you use either, make sure to check back from time to time to see if the by app method becomes available. As more and more companies become cyber-aware, they are adding MFA by app to their account options.
Would you know what to do for a ransomware attack? Download our free Ransomware Response Checklist.
The Bottomline About Multi-Factor Authentication (MFA)
- Choose MFA by app if you have the option. Don’t choose a less secure MFA method instead.
- If MFA by app is NOT available, choose MFA by text.
- If MFA by text is NOT available, choose MFA by push notifications rather than have no MFA at all.
- If you don’t have a smartphone or can’t keep it with you when you need to access your accounts, consider using a hardware token device. These devices are about the size of a USB drive and provide MFA codes when needed.
MFA by email or phone call are not considered safe and are not recommended. Most accounts have moved past offering these options because cyber criminals have learned to mimic these prompts and use them to gain access to your systems.
Looking to shore up your cyber security? We can help. Contact us or book a meeting for a free, no-pressure consultation, either virtual or in person.
Are you aware of the most common cyberattack methods?
Did you know there are over 3.4 billion phishing emails sent every day? Phishing and other cybercriminal behavior are a lot more common than you’d think.
Our free “Phishing, Smishing, Vishing, Pharming? A Cyberattacks Guide” will inform you about cyberattack methods and give you the latest in data security tips.

